Arizona Cyber Range

The Arizona Cyber Range (AzCR) is a new training and education program to provide students and trainees with a hyper-realistic environment to develop their cyber security skills against real-world attack scenarios ranging from software-level vulnerabilities to microelectronics-centric threats.
The AzCR program is run by the Secure, Trusted, and Assured Microelectronics (STAM) Center.
To learn more about AzCR’s capabilities and to explore possibilities for collaboration with your team or company, please contact us at [email protected] – Dr. Michel A. Kinsy, Associate Professor & Director of the STAM Center.
Research Highlight
Automobiles now comprise complex networks of computer systems.
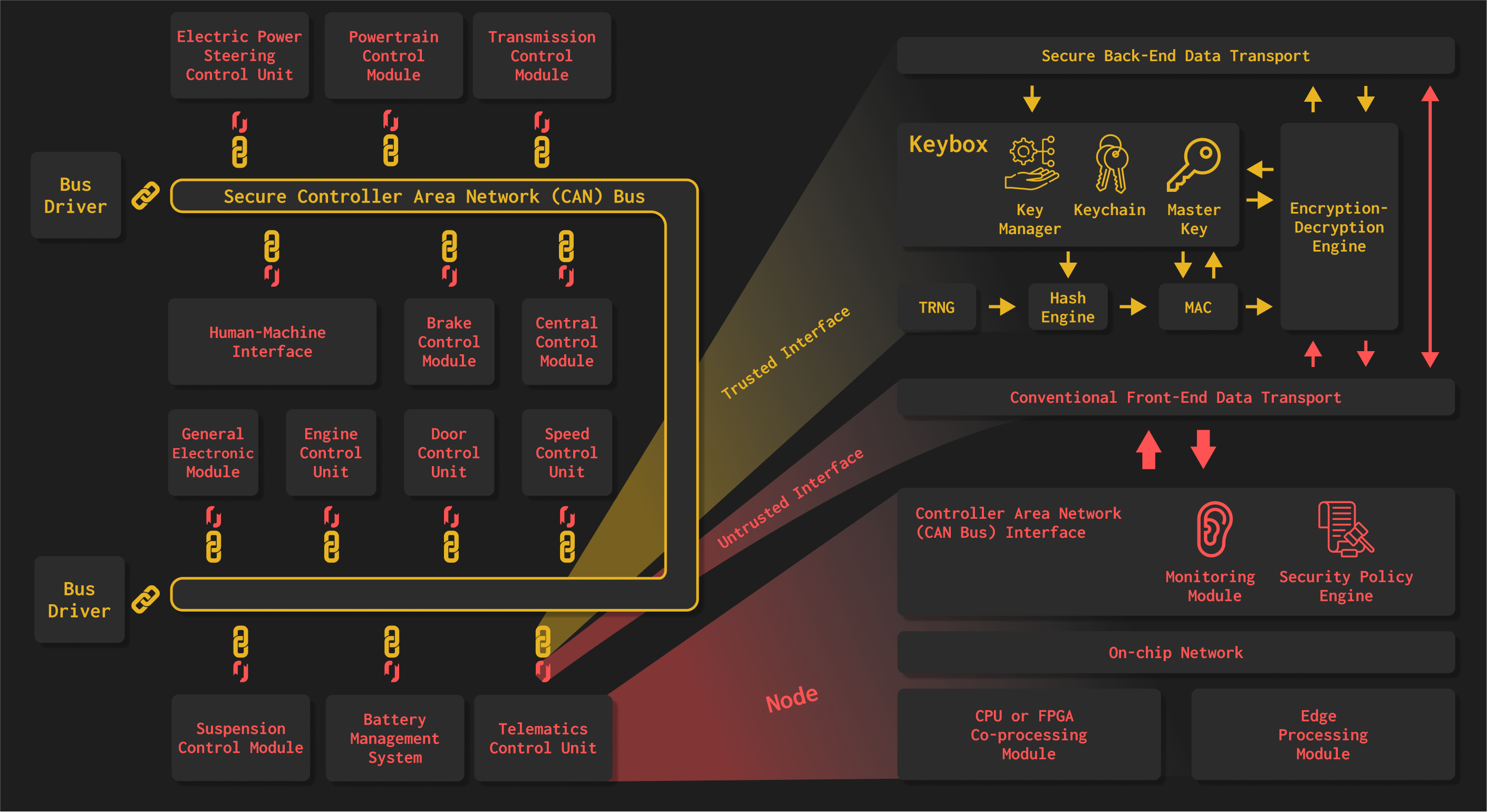
The majority of intra-vehicular communication between control units like airbags and ECUs (Electronic Control Units) occurs over the CAN bus – Controller Area Network. The CAN Bus is a legacy system rife with security vulnerabilities. With the advent of autonomous vehicles where the user surrenders more control to these computer systems, securing the CAN bus has become a critical and pressing issue.
What is the AZ Cyber Range?
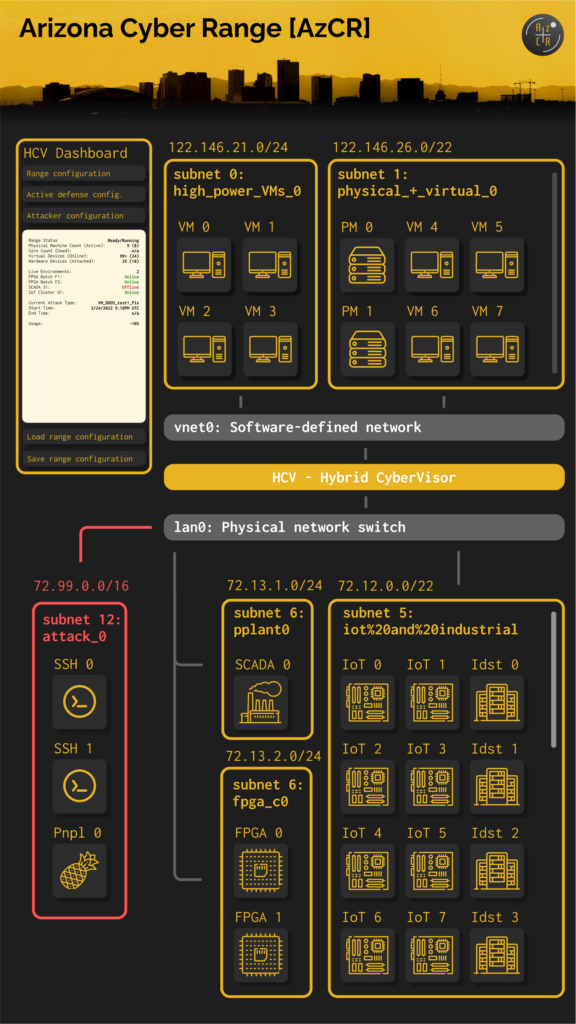
The Arizona Cyber Range (AzCR) a hybrid cyber range specifically developed as a training platform for security issues related to real hardware/electronic devices.
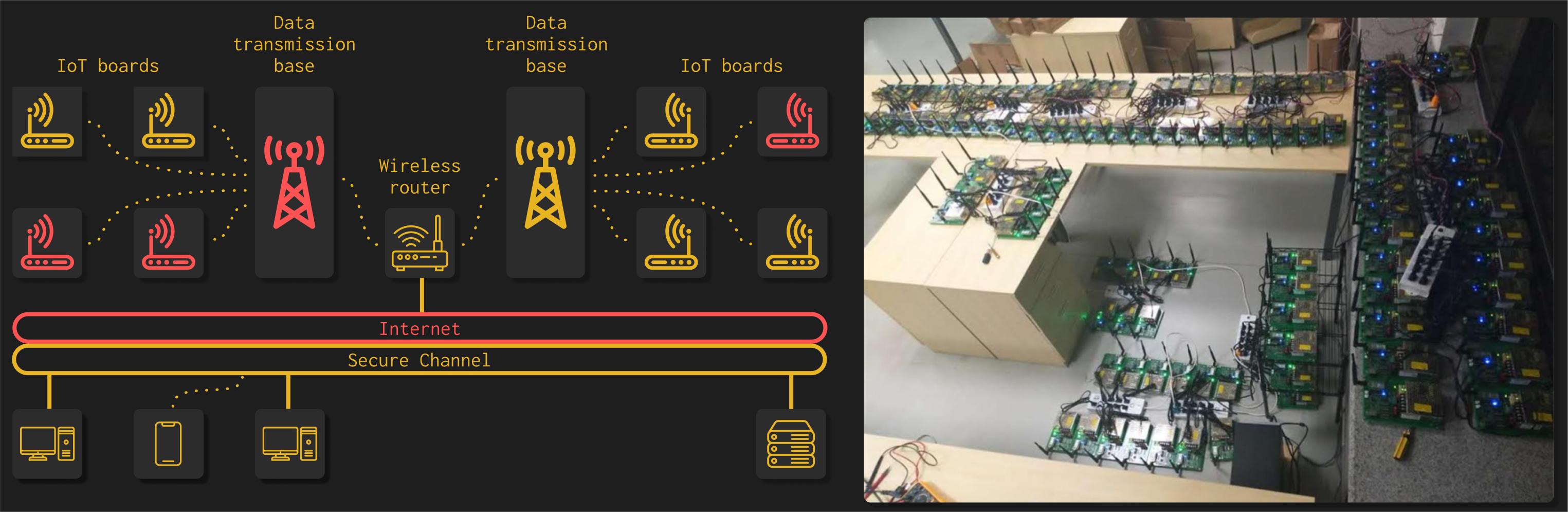
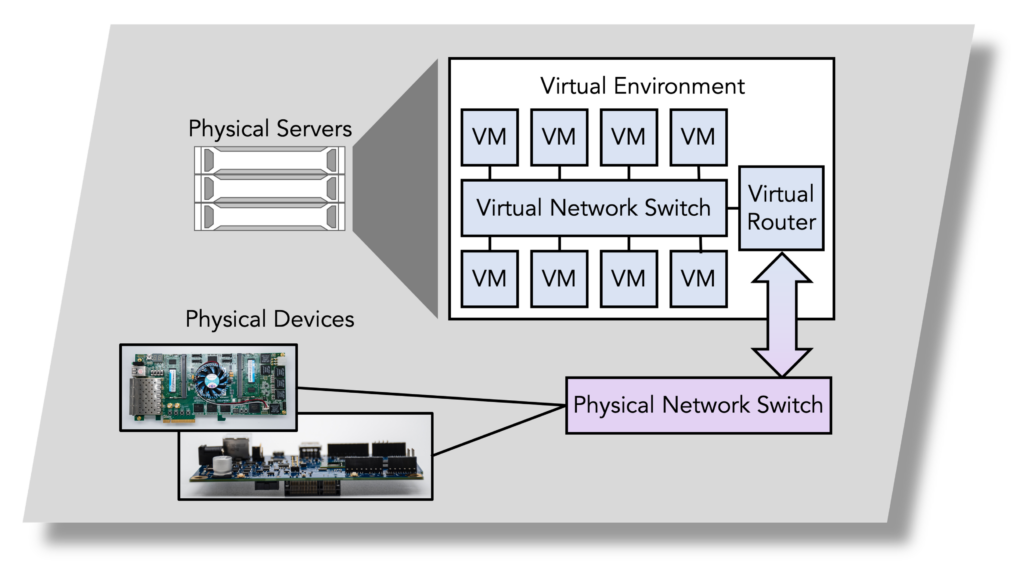
These devices are physically included in the infrastructure and made available to the trainees through the proper combinations of different virtualization services. The devices include microcontrollers, industrial control system (ICS), supervisory control and data acquisition (SCADA), field programmable gate arrays (FPGAs), Internet of Things (IoT), and industrial IoTs.

Most cyber ranges used today to train security professionals and students are pure software-based simulation environments. However, many security threats related to the hardware domain of devices are difficult to reproduce in these software environments.
Therefore, we have developed a unique capability here at ASU that combines both software and hardware aspects of system vulnerability assessment and penetration testing at different scales.
In addition to supporting the conventional software-based computer systems simulation, the Arizona Cyber Range (AzCR) provides scalability with the realism of hardware devices physically present in an emulated environment.
With AzCR, we can perform high-fidelity, hardware-in-the-loop security vulnerability assessment and penetration testing in systems at different scales – e.g., electrical power grid systems, industrial plants with different sensors, actuators, interfaces and physical processes models, and automotive Controller Area Network (CAN) bus.
With AzCR, we can provide a testbed for security validation and safety proof of concepts in cyber-physical systems (CPS).
Active System Hardening: the AzCR platform has its own, very intuitive, graphical user interface that allows:
- management of cyber agents, both virtual and physical;
- monitoring and analysis of the events and the evolution of participant agents;
- scoring to assess the sophistication of attacks and robustness of defense mechanisms;
- use of machine learning algorithms and game theory to augment the scenario entropy of cyber mission exercises.